Automatic Bug Finding
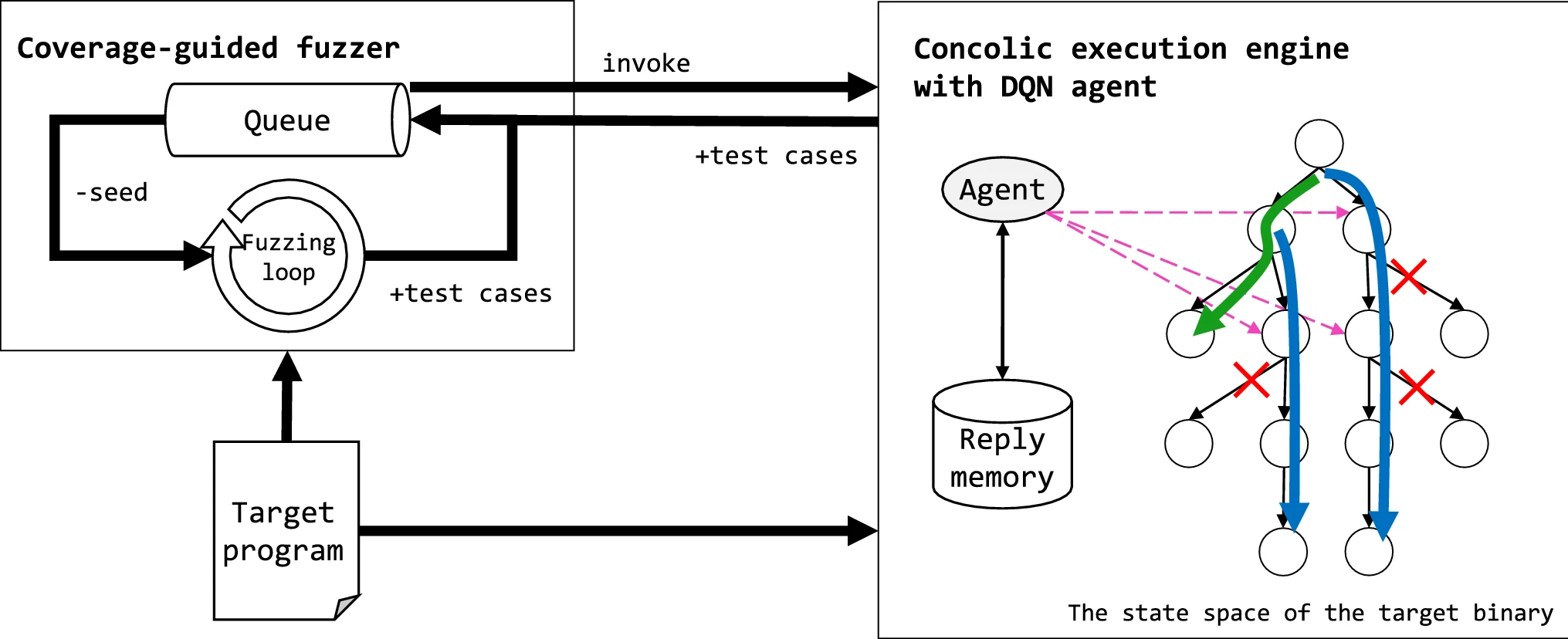
S. Jeon & J. Moon, "Dr. PathFinder: hybrid fuzzing with deep reinforcement concolic execution toward deeper path-first search," Neural Computing & Applications, vol. 34, iss. 13, 2022
Our primary interest is automatic bug finding, especially with recent artificial intelligence. Among various techniques, fuzzing is one of the most efficient method to find bugs in program. Fuzzer generates ill-formed testcases and runs a target program. When fuzzer observes crashes, it reports them with testcases. However, traditional coverage-guided fuzzers are struggle to expand code coverage when testing program. In order to address this problem, many augmenting techniques come up recently: symbolic/concolic execution and dynamic taint analysis. Along with these techniques, we try to overcome the drawback of coverage-guided fuzzer with deep learning. Deep learning provides excellent method to decide the optimal insights when fuzzer is stuck for expanding coverage. In sum up, our potential research fields in automatic buf finding are as follows:
- Coverage-guided fuzzing, Hybrid fuzzing
- Symbolic/Concolic execution, Dynamic Taint analysis
- Binary diffing
- Any study for automatic vulnerability discoverty with AI
Security for AI
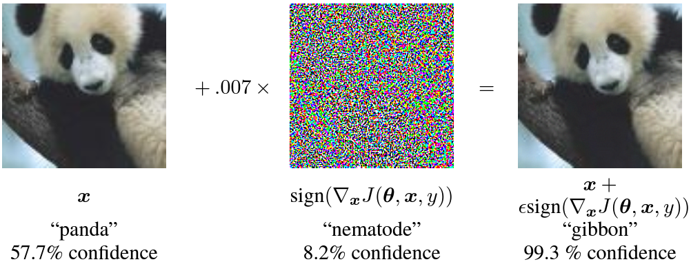
I.J. Goodfellow, J. Shelns & C. Szegedy, "Explaining and Harnessing Adversarial Examples," arXiv:1412.6572, 2014
With the advancement of AI, there are increasing attack surfaces. It is proved that most deep learning models are vulnerable to noise, even it is extremly small. So, it is important to exmaine that how must robust an AI model is. However, research regarding AI’s robustness is still at the experimental level. In this context, more and more countries and organizations require safe AI and try to legislate it. Currently, there are no dominant evaluating methods for this purpose. This provides us a great research opportunity. These are our potential research topics:
- Adversarial attack
- Backdoor attack
- Poisoning attack
- Adversarial tranining
Security with AI
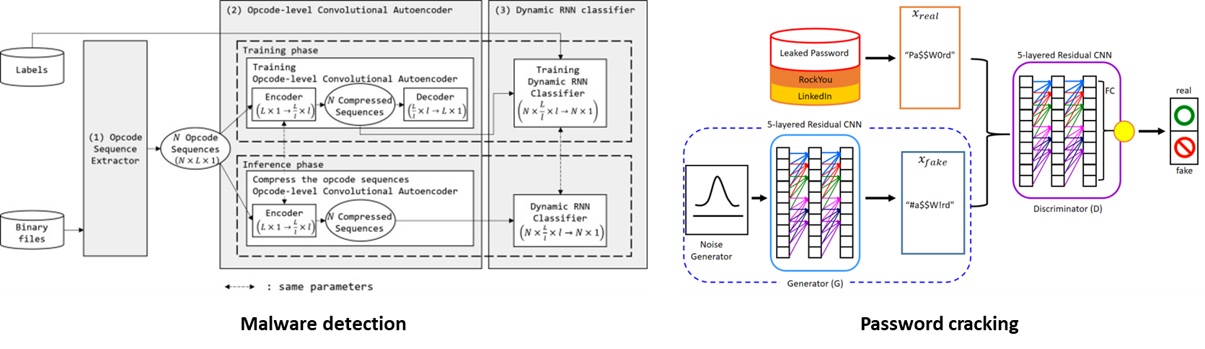
Left: S. Jeon & J. Moon, "Malware-detection method with a convolutional recurrent neural network using opcode sequences," Information Sciences, vol. 535, 2020
Right: S. Nam, S. Jeon & J. Moon, "Generating optimized guessing candidates toward better password cracking from multi-dictionaries using relativistic GAN," Applied Sciences, vol. 10, iss. 20, 2020
We also cover various security research topics with AI. The biggest advantage introducing AI in security domain is to address uncertainty of data. For example, many moderm malware have same functionality, but have different signature because of polymorphism and metamorphism. For these malware, traditional signature-based detection can be easily neutralized. With AI, however, if we properply extract features from malware, we can detect unseend malware with great accuracy. Password cracking is another example of security with AI. Modern password cracking tools such as hashcat, try to crack passwords as many as possible by generating tons of password cadidates. Most of these tools use rule sets to combine alphanumeric symbols. However, if we design password cracking model with AI, we may produce realistic password candidates without exhausting search. Other than these example, there are many interesting security research challenges which can be overcomed with AI.